Imagine losing the years of conversation cherished in an eye. This landscape is not just a digital nightmare, but there is a everyday risk without proper precautions. Protecting chat is not just about data; It is about memories, essential information and sometimes, important evidence. Their safety requires a structured approach that ensures safety and access whenever required.
Understand the importance of chat protection
Chat is often more than a casual banquet. They have emotional moments, business agreements or sensitive information. Losing them can mean losing a part of personal or business history. To know that in case of their safety, users can be persuaded to adopt continuous practices, preventing unexpected data loss or contingency deletion.
Cloud-based security methods
Cloud storage stands as the most convenient backup method. By enabling automatic synchronization with cloud services, the chat is updated regularly and preserved against phone -related accidents. This ensures that the interaction is accessible even when the device is lost or damaged. Cloud solutions provide an additional layer of protection through encryption.
Local storage as an alternative
Clouds provide local backup control, for vigilant people about privacy. They store the data directly on the device or external memory card. This method requires discipline to backup regular manual, but it prevents sensitive data from being stored externally. The restoration of local backup is straightforward, although it demands more user hard work.
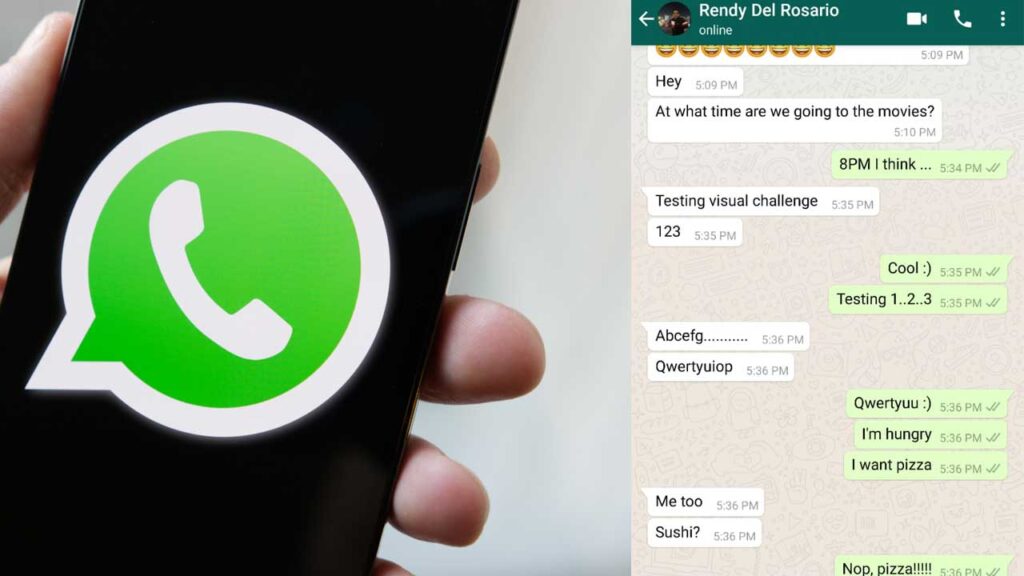
Restore the conversation
Receiving lost messages depends on the backup type. The cloud backup allows restoration through the restoration processes, where users log in, and the interaction reappears. Local storage recovery requires imports to be imported. Familiarity with the process ensures spontaneous recovery, when data loss prevents terror during stressful moments.
Encryption: invisible protector
Security is important when handling the message backup. Encrypted chats ensure that even if the data falls into the wrong hands, it remains unlimited. Most of the services encrypted automatically collected messages in both local and cloud. Understanding encryption assures users that their interaction remains private, promoting confidence in the system.
Cross-device backup challenges
Switching devices often present backup challenges, especially when walking between different operating systems. Issues of compatibility can arise, causing data loss if not carefully handled. Understanding the intricacies of device infections, including format adjustment, ensures that no message is left behind during upgrade or change.
Regular backup schedule matter
An unethical backup can result in intervals, where the data recently disappears if the data is lost. Setting a regular backup schedule prevents it, ensuring that each message is preserved. Automatic features simplify the process, but users need to verify that these settings are active. Regular checks guarantee consistent security.
Offline backup for additional safety
For maximum protection, a combination of clouds and offline methods is ideal. Offline backup, stored on external drives or safe computers, provide additional peace of mind. This dual approach is a guard against both digital and hardware failures. These files are updated regularly and are safely stored, providing broad coverage.
Data Migration: Protect everything
When transferring chat between the phone, ensure that all data successfully migrates. Each service has unique steps for this process, which requires careful execution. Mistakes or oversight can result in incomplete transfer. Perfectly pays attention to preparation and expansion that no interaction is left behind to maintain data integrity.
Handle removed messages
Sometimes, users accidentally remove significant conversations. It is necessary to understand the recovery options. Some services allow the messages removed within a limited time limit to restore if the backups are recently. Knowing these limitations and acting increases the possibility of rapidly successful recovery, which prevented significant information or loss of memories.
download app
Privacy idea in backup
Confidential concern often prevents users from enabling backups. However, most of the services provide strong security protocols. Educating yourself on these characteristics can reduce fear. Understanding where and how data is stored along with available privacy settings, gives users the right to maintain control by protecting their interactions.
Role of third-party equipment
Many third-party equipment promises that backup options increased. While some additional features provide, they come with risks. These devices are ensured to ensure that it is important and safe before use. Verified apps can offer convenience and flexibility, but caution is necessary to avoid potential data violations or loss.